8-digit BIN Issues and Risks Remain after PCI Truncation Rules Clarified
By David Gamey - 10 May 2017.
Last month we wrote this article about issues arising from the addition of new BIN ranges and the lack of clear guidance specifically with 16-digit PAN that have 8-digit BINs. Today, the PCI Council just updated FAQ#1091 "What are acceptable formats for truncation of primary account numbers?" to specifically address the issue of how to truncate 16-digit PAN with 8-digit BIN. The short answer is that PCI's first six and last 4 truncation rule applies (see below) . But, and there is a but here, not all of the issues we identified will go away.
Update: In December 2021, the PCI DSS truncation rules were changed to mitigated many issues identified in this article, for more details please see https://controlgap.com/blog/8-Digit-BINs-Great-PCI-Truncation-Reset
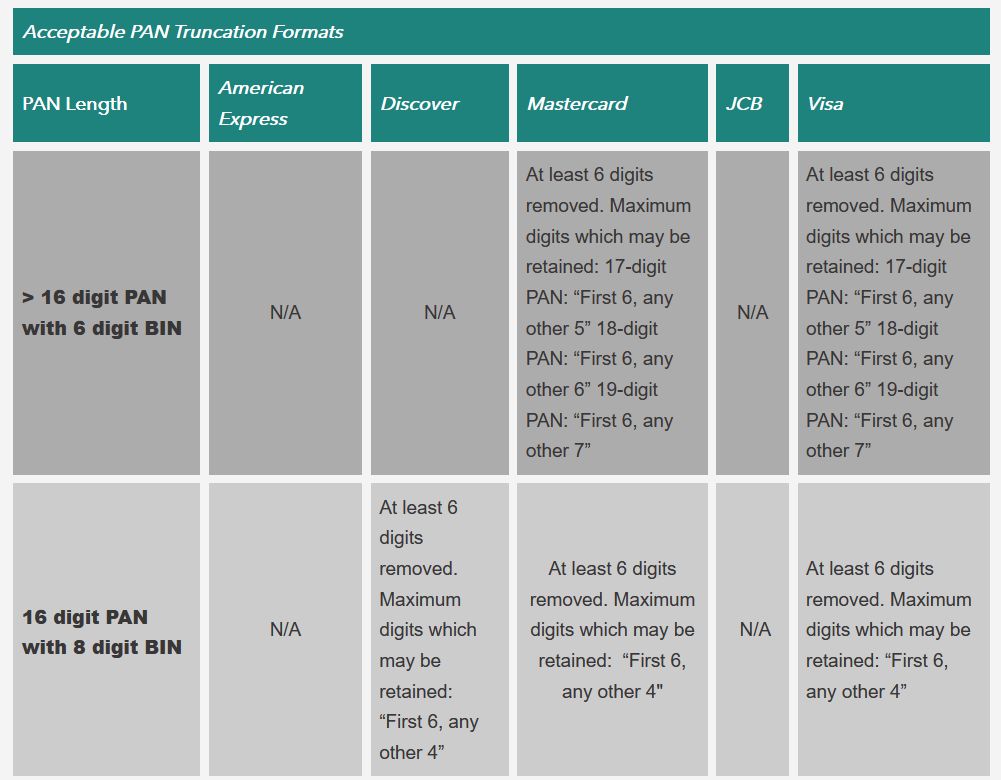
This clarification on acceptable truncation is very welcome as it provides stability to the payments ecosystem. However, organizations will still need to understand the impact of these changes on their payment systems. Guidance from the brands is also clear that relying on truncation alone will not be sufficient to protect the data if more digits are kept.
- For organizations that do not need to keep the full BIN, there should be little if any impact and should be able to continue to use 6&4 truncation. They should however validate this to ensure there are no unpleasant surprises. We expect the majority of merchants will be in this group.
- Some organizations will need to keep the full BIN. They will need to take additional steps (e.g. encryption, tokenization, etc.) to protect that information while stored. In many cases this could introduce additional data elements that impact PCI DSS scope or the number of applicable requirements within their scope. Organizations need to carefully evaluate the impact and implement changes to ensure they stay compliant. These are changes that, if implemented without considering compliance, could require substantial remediation.
Lastly, we urge caution if you are using 6&4 truncation when these new PAN/BIN ranges go live. Specifically, we recommend that you monitor the risk of correlating truncated data to PAN considering both internal and external factors. Why? Because, we believe there may be additional risk here depending on how the Card Brands and Issuers allocate these BIN ranges. And while these are primarily risk questions for those organizations, you should also be aware of the risk. If you can live with more aggressively truncated PAN that will help to address this risk.
For example, consider the following approach which assumes an attacker can get 6&4 truncated PAN from your organization and a separate list of 8-digit BINs that are allocated and/or in use. The correlation risk will depend on how many of these BIN ranges match in the first six digits. If the BIN ranges are sparsely allocated there will be fewer 8-digit BINs with the same first 6-digits and correlation will be much easier than if the 6-digit ranges are densely allocated. Using fictitious examples from the previous article to bound the risk:
| PAN | Rule | Truncation | Strength | Compliance |
|---|---|---|---|---|
| 9234567890123455 | 6-4/16 | 923456xxxxxx3455 | 1 : 100,000 | PCI 3.2 |
| 9234567890123455 | 8-4/16 | 92345678xxxx3455 | 1 : 1,000 | Not PCI 3.2 compliant |
As you can see, depending on how sparsely the 8-digit BINs beginning 923456 are allocated, the strength will vary considerably. It is also clear, that anything less than full allocation reduces the strength.
| Number of BINs in 923456xx | Strength |
|---|---|
| 100 | 1 : 100,000 |
| 50 | 1 : 50,000 |
| 25 | 1 : 25,000 |
| 10 | 1 : 10,000 |
| 1 | 1 : 1,000 |
For a more detailed discussion of the issues please read our original article.