PCI DSS v3.2 - What You Need to Know to Stay PCI Compliant
By Neal Christopher - 08 Jun 2016.
To accept credit cards in Canada, businesses need to be PCI compliant. Becoming PCI compliant can be difficult in the first place and keeping up with the changes even more so. In April 2016 the Payment Card Industry (PCI) Security Standards Council (formed to regulate security for the payment card industry) released an updated list of compliance requirements known as the PCI Data Security Standard (DSS) v3.2.
Let us guide you through these new requirements. We found thousands of wording changes, most of them innocuous and helpful clarifications, however, a small handful of these changes will require some serious attention in order to maintain compliance after October 2016. The rest of the new requirements are considered best-practice until they become mandatory on February 1, 2018.
Continue reading for everything you need to know about PCI DSS v3.2.
What Are the Largest Impacts of PCI DSS v3.2?
Service Providers
A large number of the new requirements are focused on service providers and these will take significant effort to implement and maintain. Service providers will want to start working towards these new requirements as soon as possible in order to be successful.
Multi-Factor Authentication
Multi-factor authentication is now required for all admin personnel accessing the Cardholder Data Environment (CDE) network or individual systems within the CDE. We see this as the single largest change in v3.2 requiring both merchants and service providers to implement new technical security controls.
E-Commerce Web Redirection
E-commerce web redirection servers are back in scope. The PCI SSC announced in their May 2016 assessor newsletter that updates to Self-Assessment Questionnaires SAQ-A, and SAQ-A-EP now have a number of increased requirements to address highly targeted merchant e-commerce web redirection servers. This means e-commerce web redirection servers (using iFrame or Full URL redirection) are back in scope when using SAQ-A eligibility requirements, and third-party web hosts that host these servers are considered third-party service providers under req. 12.8. This redirection scope applies to all entities using either Self-Assessment Questionnaires (SAQ) or Reports on Compliance (ROC) for compliance validation. We anticipate that the related PCI SSC redirection FAQ’s will be updated to clarify this position.
What Is the Difference Between PCI DSS v3.1 and PCI DSS v3.2?
In addition to the thousands of wording changes and 14 numbering changes, there were:
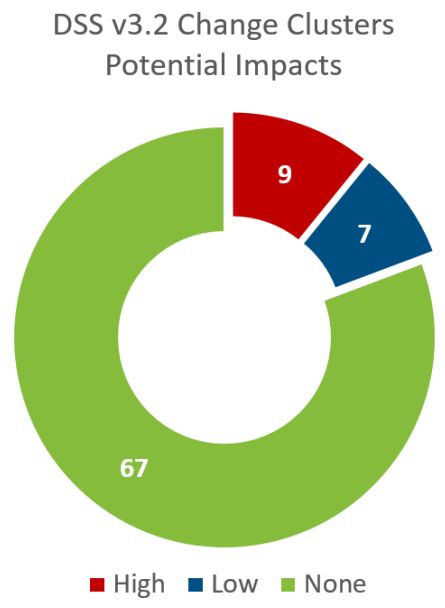
83 Total Discrete Change Clusters
- 67 of these changes have an impact rating of None. These changes have a negligible impact on compliance and help to improve clarity and understanding on intent.
- 7 of these changes have an impact rating of Low. These changes have a low impact on compliance and are a new incremental change that potentially alter compliance efforts.
- 9 of these changes have an impact rating of High. These changes have a high impact on compliance and are typically a new requirement or involve potentially significant effort to achieve or sustain compliance.
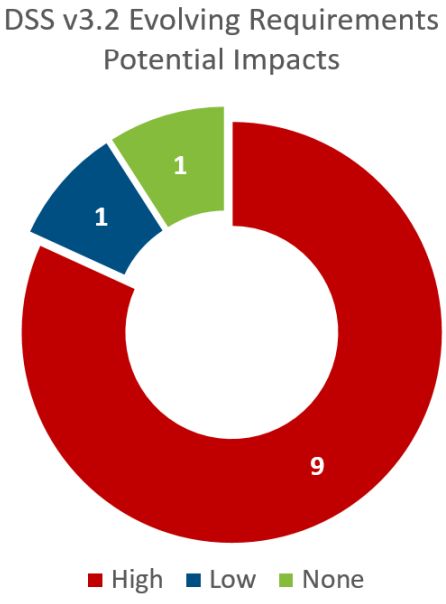
11 Evolving (New or Changed) Requirements
- 1 of these changes have an impact rating of None (#49 in our change analysis documents)
- 1 of these changes have an impact rating of Low (#21 in our change analysis documents)
- 9 of these changes have an impact rating of High. These are new requirements added and are effective as of Feb 1, 2018.
There are several other significant differences between PCI DSS V3.1 and PCI DSS V3.2. To see a quick overview of the rest of the changes, read our Change Analysis Brief. If you would like to know every word that changed, read our Change Analysis Document.